New features in cockpit webapplication:
- Greatly improved layout
- Editing process variables
- Cancelling a process instance
- Increment retries for failed jobs
- Login based on Process Engine Identity Service
- Managing users & groups based on the process engine engine identity service
- Creating an initial user for a process engine
- Improved variable handling
- Added Jobs resource (contribution by Clint Manning, 1&1)
- Added User and Group Resources
- Started work on authorization service
Additions to the Webapps
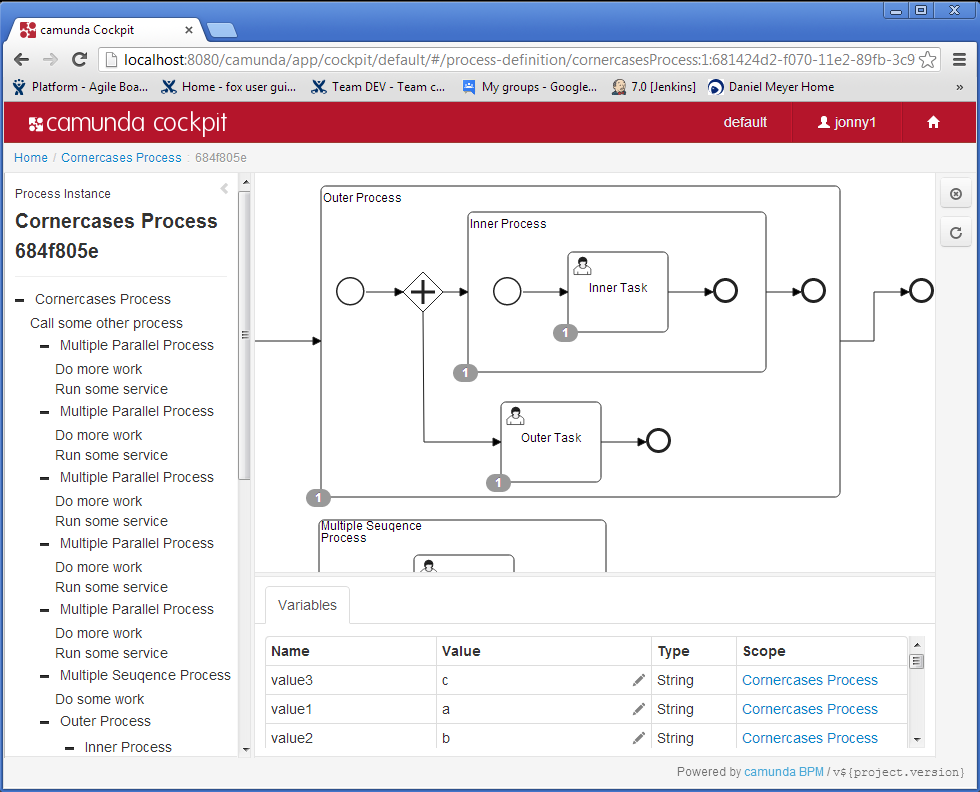
Editing process variables:
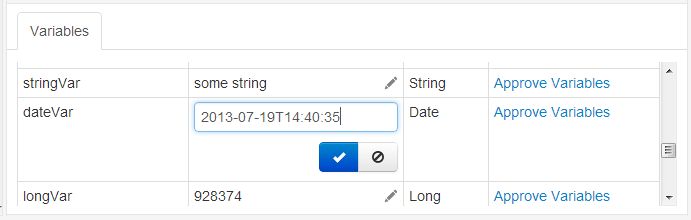
Cancelling Process Instances:
Increment Job retries
Selecting a process engine
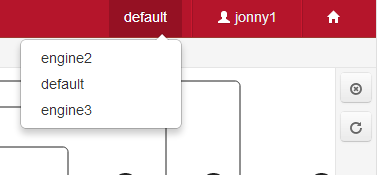
Switching to a different application
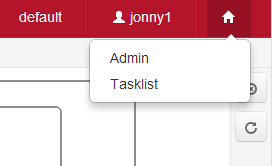
The camunda Admin application allows managing Users and Groups
Started Work on Authorizations:
The authorization service allows managing <a href="https://docs.camunda.org/latest/guides/user-guide/#process-engine-authorization-service">Authorizations</a>.
Authorizations manage permissions of a given user/group to interact with a given
resource.
Creating an authorization
An authorization is created between a user/group and a resource. It describes
the user/group’s permissions to access that resource. An authorization
may express different permissions, such as the permission to READ, WRITE, DELTE
the resource.
Granting / revoking permissions
In order to grant the permission to access a certain resource, an
authorization object is created:
Authorization auth = authorizationService.createNewAuthorization(); //... configure auth authorizationService.saveAuthorization(auth);
auth.setUserId("john");
-OR-
auth.setGroupId("management");
auth.setResource(Resources.USER);
auth.setResourceId("mary");
auth.addPermission(Permissions.READ);
authorizationService.saveAuthorization(auth);
referenced process definition.
Checking a permission
Permissions can be checked using a query:
authorizationQuery.userId("john")
.resourceType("processDefinition")
.resourceId("2313")
.hasPermission(Permissions.READ)
.hasPermission(Permissions.WRITE)
.hasPermission(Permissions.DELETE)
.list();
Permissions for the user “john”.
